WordPress has a new addition to its library of rogues. This malware outbreak is known as WP-VCD. An in-depth report by Wordfence shows how closely they’ve been following it. Wordfence divulges all the details of how this gang works, why it’s hard to battle with and to what extent it’s spread.
How does WP-VCD Malware get on my site?

Usually WordPress sites get hacked through your outdated plugins. Not this one though. Hackers have upped their game and now they use you to get your website. They do this through pirated plug-ins available on websites ranking above the legitimate websites. These download sites use black-hat SEO tactics to get high up in search results from amped-up keywords using the WordPress sites that have already been compromised. Here’s an example of how it works, making victims fall for it regularly. Here’s the result when I searched for a popular WordPress plug-in:
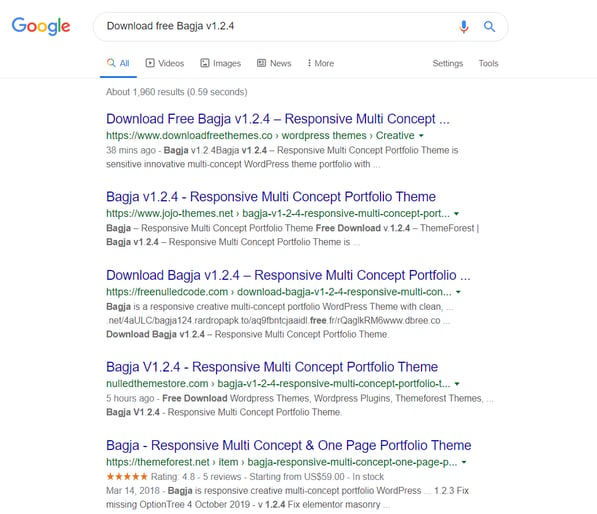
They specially offer nulled themes or plug-ins not available on the original WordPress sites.
What kind of a threat does WP-VCD Present?
When these corrupted themes are downloaded, your WordPress installation gets hacked and taken over. A backdoor account name (Username: 100010010 Email: te@ea.st) is added to each one of the compromised sites. Hackers could easily access the installations as a registered user after that. In case you wish to uninstall the corrupted theme, it would be too late, because this infection will spread to all the other themes just in case you do remove it by any chance. If it’s a shared hosting environment, it’s a double treat for the hackers, as they could easily move to other websites on the same server.
What’s their agenda?
Of course, you probably don’t have any mortal enemies who’ll rejoice at the prospect of invading your website and taking over it (well, maybe you do). Hackers earn from their malvertising campaigns and inserting keywords and back-links that lead to their sites. This boosts their sales and their visibility. But… even if you don’t have any mortal enemy, you wouldn’t want robbers using your house to sell their goods while you sit and watch as they take over.
When did it all start?
This first began in February 2017. It popped up a few times and was squashed, and it popped up again, each time more advanced than the previous version. Mikey Veenstra, author at WordFence says, "According to malware scan results across the Wordfence network, WP-VCD is installed on more new sites per week than any other malware in recent months”.
How do you get rid of a WP-VCD Hack?

Fortunately, thanks to an in-depth analysis, the team has a clear understanding of how to tackle WP-VCD Hacks. So, the first step would be:
- www.download-freethemes.download
- www.downloadfreethemes.co
- www.downloadfreethemes.space
- www.downloadnulled.pw
- www.downloadnulled.top
- www.freenulled.top
- www.nulledzip.download
- www.themesfreedownload.net
- www.themesfreedownload.top
- www.vestathemes.com
2. Avoid downloading any obsolete themes or plug-ins
3. If your site is already infected, contact the Wordfence cleaning team to have it back up and running safely. This report has a complete appendix of the indicators of compromise.
Also a general rule of thumb is to only download highly rated and popular themes and plugins from legit websites like Themeforest and the main WordPress site. If you must download plugins from places elsewhere do a background check with your IT staff to make sure these are legitimate sources.
Next Steps
Having WP-VCD Malware on your site is serious business. Not only are you putting your own site at risk, there’s a chance you might be infecting other people, files or applications that are on the same server as your website. Feel free to contact us for a complimentary security assessment and let you know options to remedy.




